In the realm of cybersecurity, the phrase "the devil is in the details" rings especially true. One of the most compelling examples of this is the capture of the notorious BTK killer, a serial murderer who eluded law enforcement for decades. His eventual downfall was not due to a dramatic confrontation or an eyewitness tip, but rather through the seemingly mundane details found in metadata. This article explores the critical role of metadata in the BTK case and highlights how tools like Metagoofil can be leveraged in modern cybersecurity efforts.
The BTK Killer and the Power of Metadata
For more than three decades, the police couldn't manage to arrest the BTK killer. However, authorities finally caught Dennis Rader in 2005 while he was driving near his home in Park City. After the killer's arrest, the nation learned about the heinous crimes he had committed over the years. Dennis Rader, known as the BTK killer (Bind, Torture, Kill), terrorized Wichita, Kansas, from 1974 to 1991, committing a series of brutal murders. For years, he managed to evade capture, taunting law enforcement with letters and clues. His confidence grew, leading him to make a critical error that would ultimately expose him.

I will not be talking about the BTK killers’ victims. I will be discussing the methodology used to unmask him.
In January 2005, Rader left a package for Wichita’s KAKE-TV inside a cereal box, which he placed in the back of a pickup truck in the parking lot of a local Home Depot store. The owner, however, thought it was garbage and threw it out. Rader then contacted the station, asking if they had received the package. It was later found in the trash, and police were able to review security camera footage that showed a person driving a black Jeep Cherokee dropping off the package.
In a subsequent message to police, Rader asked them, “Can I communicate with Floppy [disk] and not be traced to a computer? Be honest.” If so, he told police to place an ad in The Wichita Eagle with the message, “Rex, it will be OK." Two weeks later, a disk arrived in a package sent to KSAS-TV with a file that contained instructions to detectives about further communications. What Rader didn’t realize was the disk also contained encrypted metadata that would lead police straight to him.
In 2004, Rader resumed communication with the media and the police, sending a floppy disk to a local news station. He believed that erasing files from the disk would cover his tracks. However, investigators were able to extract metadata from the disk, which included a deleted Microsoft Word document. This document contained metadata revealing it had been last edited by a user named "Dennis" on a computer registered to "Christ Lutheran Church."
The disk was handed over to Officer Randy Stone of the Wichita Police Department, who was skilled in computer technology. According to The Wichita Eagle, he used a forensic software program to call up deleted files and other hidden data that showed where and when the disk had been last modified. It revealed the disk had been used on a computer at Wichita’s Christ Lutheran Church by a user named “Dennis.” Upon looking up the church's website, they found "Dennis Rader" listed as the president of the congregation. After locating his home address, police drove by and saw a black Jeep Cherokee in his driveway.
After matching Dennis Rader’s DNA to evidence found at several of the crime scenes, police arrested him on February 25, 2005. During his interrogation, Rader expressed his anger at police for lying to him about his floppy disk being traceable. “I need to ask you, how come you lied to me? How come you lied to me?” Rader admonished Lieutenant Ken Landwehr, commander of the Wichita Police Department’s homicide unit. “Because I was trying to catch you,” Landwehr replied. This small piece of information provided a crucial lead. Law enforcement cross-referenced this data with local records, leading them to Dennis Rader, a respected member of the community and church president. DNA evidence subsequently confirmed his identity as the BTK killer, ending his reign of terror.
What is Metadata?
Metadata means "data about data". Metadata is defined as the data providing information about one or more aspects of the data; it is used to summarize basic information about data that can make tracking and working with specific data easier.
Some examples include:
- the Means of creation of the data.
- purpose of the data.
What information can be revealed with Metadata?
The BTK case underscores the significant role metadata can play in forensic investigations. In the digital age, extracting and analyzing metadata is a cornerstone of cybersecurity. Tools like Metagoofil have become invaluable in this effort. Metagoofil is an open-source tool designed to extract metadata from public documents. By scanning files such as PDFs, Word documents, and images, Metagoofil can reveal hidden information about the document’s creation, modification, and authorship. This can include usernames, software versions, file paths, and other details that can be critical in both offensive and defensive cybersecurity operations.
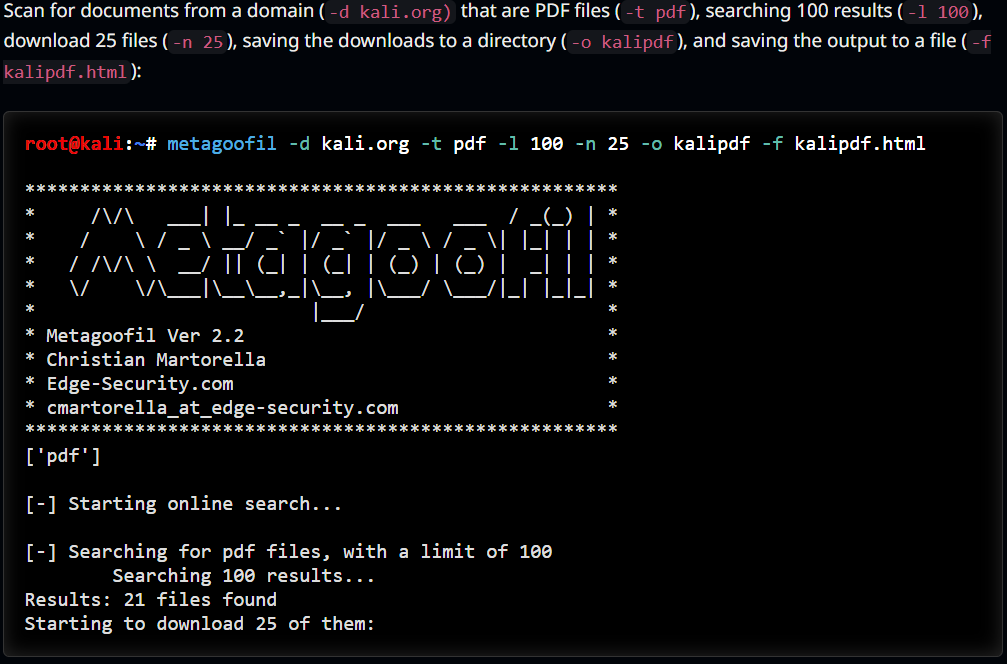
Applications of Metagoofil:
-
Penetration Testing: Cybersecurity professionals can use Metagoofil to gather intelligence about a target organization. By analyzing metadata from publicly available documents, they can identify potential vulnerabilities, software in use, and internal file structures.
-
Incident Response: During a security breach investigation, Metagoofil can help trace the origin of malicious documents or emails. Metadata can reveal the author’s identity, creation dates, and even geographic locations.
-
Data Leak Prevention: Organizations can use Metagoofil to audit their own documents before they are released to the public. This helps ensure that sensitive information is not inadvertently shared through metadata.
-
Compliance and Auditing: Regulatory requirements often mandate the tracking of document handling and modification. Metagoofil can assist in compliance efforts by providing detailed metadata reports.
The capture of the BTK killer through metadata analysis serves as a powerful reminder of the hidden value in digital footprints. As cybersecurity threats continue to evolve, the ability to unearth and interpret metadata becomes increasingly vital. Tools like Metagoofil equip professionals with the means to uncover these invisible details, bolstering defenses and enhancing investigative capabilities. In a world where every byte can tell a story, mastering the art of metadata analysis is an essential skill for any cybersecurity arsenal.

